** Note from Matt **
Recently, our site was hacked. We were being told by customers and readers that our site was redirecting them to “adult” sites. We were losing sales, we were losing visitors, and we just generally looked bad to any new visitors coming to our site…
We panicked a little and hunted for a solution to this. We couldn’t find any articles or information about this issue. Then, due to the amazing power of Facebook groups, a magician named Chris Moore popped up to save the day.
Chris quickly cleaned up our sites and put some security measures in place to prevent these types of issues from happening again in the future.
Seeing as we couldn’t find a solution to this problem through our own searches, we begged Chris to write an article for our readers on how to solve and prevent this issue.
So, without further ado, here’s Chris’s (insanely in-depth) solution. Make sure you follow along and implement everything he recommends on your site!
** Enter Chris Moore **
Your super awesome, highly targeted, and hyper-clicked ads are running on Facebook and Twitter. Tons of people are visiting your site. All seems to be going well. Except that conversions are kind of low. “Hmmm… My ads don’t normally have this lackluster response, what’s going on?”
And then it gets worse, now you have angry visitors beating down your inbox door with outrageous claims that your links are redirecting them to porn sites! “What? How did this happen? What’s going on? Did I get hacked?”
You fire up your browser, click on your link, and… nothing. It just goes right to your site. So you scratch your head thinking, “Oh well, maybe it was just a coincidence.”
But it wasn’t. Another email or Facebook message comes in, and then another… Now they’re saying it only happens on mobile devices. So you crack out your iPhone and sure enough, straight to porn! “Ah man… I’ve been hacked!”
So how did you get here?
Well, there are a ton of ways: being victim to SQL injections; using weak passwords, which lead to a brute force login; having themes or plugins with vulnerabilities (it even happens to experienced developers!); not updating the WordPress core (especially when security issues are patched); and being the target of a hacker who has your site on their mind (and honestly, there isn’t much you can do there, especially if they are really good).
But more important than knowing the causes and methods, the real question is this: how can you prevent this from happening in the future? That’s what this post hopes to enlighten you on.
The 11 Steps Along the Path to Security Bliss
Here are a series of steps that you should take to protect yourself from a future hacking or malware infestation. Please note that these are not all the steps you can take, but these are very good ones, and will have you headed in the right direction.
You should also take these steps before you contact your host, or a professional, to help you to clean up your sites from a prior hacking. If possible, you should aim to complete these steps in the course of one day. If that simply isn’t possible (due to the number of sites you have), consider hiring some help, or set yourself a schedule by which you can complete these steps as soon as humanly possible.
And of course, if any of these steps feel too daunting or intimidating, or you just want things to be cleaned up and locked down for you, please feel free to get in touch with me here: https://theopguru.com/malware-cleanup/. I would be happy to serve you further!
And with that, on to the 11 steps!
1.) Backup, Backup, and Backup Again
If you don’t already have a backup routine, let’s make sure you have one starting now. Some hosts are kind enough to do daily backups for you (such as SiteGround and a number of other hosts, sometimes depending on which plan you have), but even if they do, you should never rely on just that.
I personally like to have 3 main locations for my backups at all times: my host’s backup (which is already on my server); an Amazon s3 backup; and a DropBox backup. You can of course use any service you want (and there are many, both free and paid), but the bottom line is you need to have multiple backups, in multiple locations. Just trust me on this.
Additionally, you should download any cloud-based backups to your desktop computer at least once every week or two, just in case. Paranoid, you say? Possibly, but it’s always better to be safe than sorry. (Remember that paper you wrote back in high school, the night before it was due? You were right about to finish it, and then, at the worst possible moment, the power went out, and you hadn’t saved it yet! Well, that happened to me a few decades ago and from that day forward I was never the same! Let us learn from our mistakes (or mine, in this case)).
(We use BackupBuddy for backups at Learn To Blog)
2.) Clean Up Yo Mess!
You will see a theme throughout this entire post, namely, we should try to keep our sites and servers as lean and clean as possible. Start by getting rid of all unnecessary clutter and stuff just lying around. For this step, I would like you to completely delete and remove any and all WordPress sites (the entire folders!) that you do not actually use or need. Just remove them completely. If you would like to keep them for the future, just go into your cPanel (specifically your host’s Control Panel > File Manger), then ZIP the folder associated with that site, download the ZIP, and then delete the original folder and the ZIP. This will save you from a lot of the work to follow below.
3.) Purge Unneeded Users and Demote Others
Delete all unused administrator level user accounts. This includes anyone with administrator privileges that doesn’t need them anymore: previous developers, former colleagues, etc. Also consider demoting anyone that doesn’t actually need administrator level access. Just go to WordPress > Users > Edit > Role, and then change the user role to either Editor, Author, or even Contributor (you can find out more about WordPress user capabilities and roles by clicking here).
4.) Delete the User with the Username “Admin”
“Admin” is the most common username, and it is also the most commonly attempted username in brute force login attempts. And although it isn’t difficult for someone to find out your username, why give it to them on a silver platter or expose yourself to the more bot-drive, automated attacks?
So, if you have a user with the username “admin”, login with another administrator account and delete that user. When you delete this user, it will ask you to assign all content to another user. Make sure to do so or you will lose all content created by that user! This is a very important step, so please don’t miss it! Again, make sure to assign the content created by that “admin” user to another user, or you will lose everything! Okay? Okay.
5.) Get Rid of Keepsakes
Human beings seem to have a tendency to hold on to things they don’t actually need. Well, with your WordPress site, this can be deadly (especially if you don’t have a backup). In this step, you should proactively delete any and all unused or deactivated plugins or themes on all of your sites. Get rid of the clutter. (Some choose to leave the Twenty Twelve theme as a backup theme, just in case, but that is up to you).
6.) Update, Update, and Update Again
This is probably the number one cause of your site getting hacked: not keeping up to date with WordPress, theme, and plugin updates. Almost every day new vulnerabilities are being discovered in WordPress themes and plugins (mainly plugins). Responsible and engaged developers are quick to patch these issues (sometimes even before the vulnerability is publicly known), and so we should be vigilant to update as soon as a new update arrives. I appreciate that sometimes updates can mess up your site (and I have dealt with this on my own sites at times), but please don’t let that stop you from updating, especially if the update concerns a security issue.
So, in this step, you should update all WordPress installations on your entire server, as well as all themes and plugins, to the latest versions. Yes, do this for every single WordPress site on your server. This step is absolutely essential, and as I said above, it’s probably the cause of most hacking and malware related issues in the first place!
7.) Change All Your WordPress Passwords
If your site was compromised, chances are that the hacker was able to get your password (either by a brute force attack, or after-the-fact, through other means). Regardless, it is a good habit to update your passwords every 3 – 6 months (I know, I know, it’s a hassle, but we want to be safe, right?).
So, in this step, change all the passwords for all of the remaining administrator or editor level users on all of your WordPress sites. Passwords, as a rule, should be “strong”, which means they should be unique, long, and obscure. Resist the urge to use short or duplicate passwords across your sites. Use programs like “1Password” or “LastPass” to manage all your passwords. You will thank me later for that suggestion. 🙂
8.) Limit the Doors of Entry
As you can see, there’s a theme developing here: if you don’t need it, get rid of it! In this step, I’m asking you to delete all FTP user accounts that are not needed. I personally only keep the main one and any accounts that are being used by a developer (which I will delete when the job is done).
However, when you do this, please make sure to keep the FTP content folders for any FTP users that you delete. The system should prompt you to keep the content and folders, so make sure you do so. I repeat, only delete the user itself, and not the content folders, or you will lose your content!
9.) Change Your Remaining FTP, cPanel, and Hosting Passwords
Now that you’ve gotten rid of the unnecessary clutter in your FTP accounts, you should change all the passwords for all the remaining FTP accounts, as well as the passwords for your main hosting account and cPanel. As mentioned above, passwords should always be unique, long, and obscure. Again, “1Password” and “LastPass” are your friends here.
10.) Ensure that File and Folder Permissions are Correct
If your host is worth being hosted with, they will do this for you. I have seen cases (a few, unfortunately), where the host will tell you you have to do this yourself. But since this is a really simple thing to do, I can’t image that a good host would push this task back on you. If that does happen though, even after you call and tell them you can’t figure it out, I would seriously consider changing hosts. But hopefully they will cooperate with you on this.
So, in this step, please call your host (or submit a support ticket) and ask them to verify the permissions for all files and folders on your server. Files should be set to 644 permissions and folders should be set to 755 permissions. This is the WordPress default and standard. You would be surprised how many insecure and crazy permissions I have seen while cleaning up hacked sites. Just double-check and be on the safe side.
11.) Install the Free WordFence Security Plugin
This step is probably one of the most critical in this entire series of steps, and that’s why I’ve saved it for last. WordFence Security is a godsend and a truly wonderful tool. Yes, there are many security plugins out there, and some may actually do more and have a fancier interface, but WordFence is not only free and effective, it is also fairly easy to use. Bottom line is, it gets the job done. Install it now.
Once you’ve installed it, please take the following steps (and this is the whole point of installing WordFence right here):
Go to WordFence > Options and set all your settings like the following screenshots (feel free to customize, but I would select all of the scan settings for sure though):
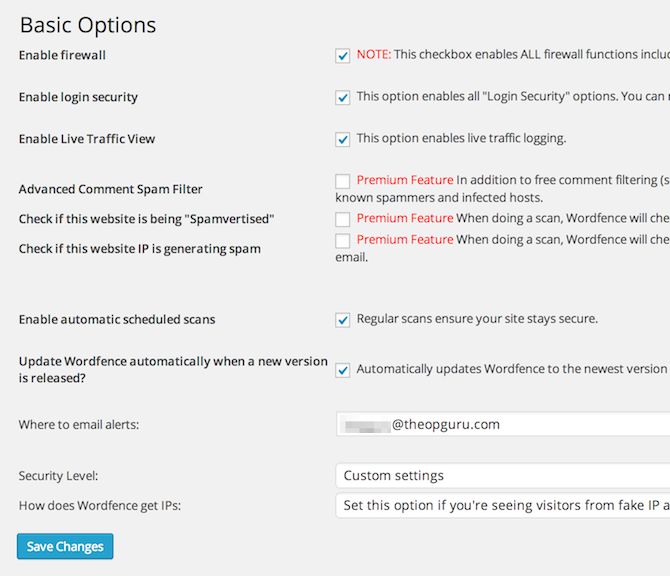
WordFence Basic Options
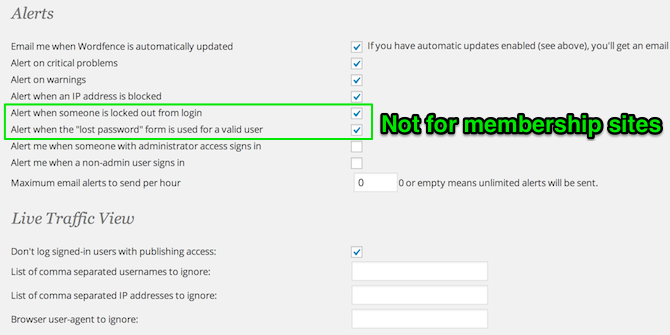
WordFence Alerts
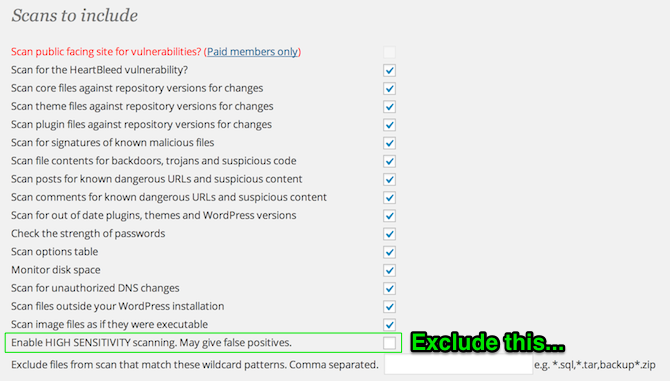
WordFence Scan Settings
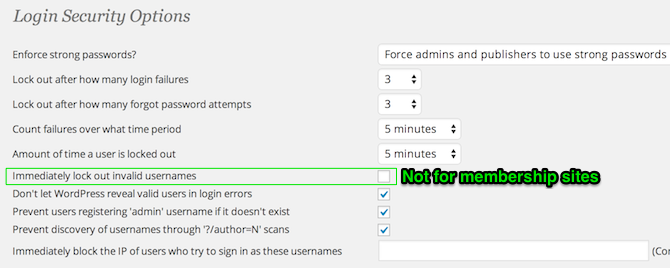
WordFence Login Security Settings
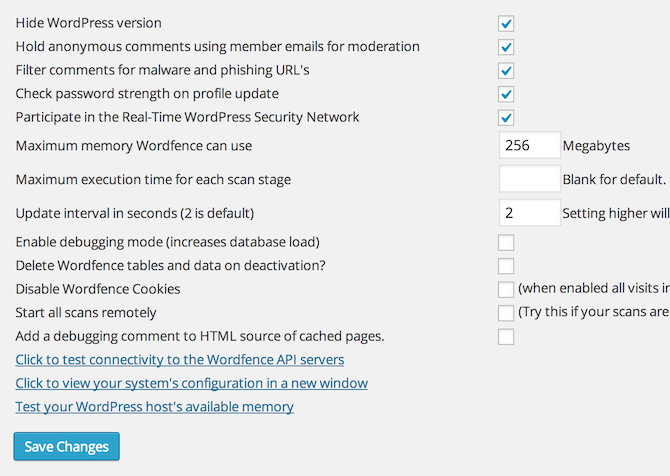
WordFence “Other” Options
Once you have mimicked those settings, go to WordFence > Scan > Start a WordFence Scan.
The scan will take some time, but will yield some very useful information. Once you get the report, you may want to click on “Restore the original version of this file” for any warning that WordFence gives you, or you may just want to delete the plugin/theme in question altogether and reinstall it. It is entirely up to you and depends on your site and setup. Good thing you have backups though, right?
12.) 3 Powerful .htaccess Rules (for Advanced Users)
Yeah, I know, there are only supposed to be 11 steps, but I felt it would be a disservice to not include these powerful .htaccess rules that will further lock down your site from attacks. If you don’t feel comfortable doing this, please don’t. Reach out for help from a professional instead. If you do feel comfortable though, then dive on in, because these 3 rules alone will do wonders for your WordPress site’s security.
In the root folder of every WordPress installation you have, you should find an .htaccess file. If you don’t see it, it’s probably because your FTP client or cPanel settings aren’t configured to show “hidden” files. Ask your host about this. Once you find the .htaccess file, open it, and add the following lines to it (at the very bottom or very top should be fine):
# protect wp-config.php file <files wp-config.php> order allow,deny deny from all </files>
Those lines of code will protect your “wp-config.php” file, which is one of the most commonly hacked files that we see in the WordPress world.
# disable directory browsing Options All -Indexes
That code disables the ability to browse website directories directly, which hackers may use to find exploits to help them get into your system. Can they still find other ways of getting information? Of course they can, but again, why make it easier for them to do so?
# protect from sql injection
Options +FollowSymLinks
RewriteEngine On
RewriteCond %{QUERY_STRING} (\<|%3C).*script.*(\>|%3E) [NC,OR]
RewriteCond %{QUERY_STRING} GLOBALS(=|\[|\%[0-9A-Z]{0,2}) [OR]
RewriteCond %{QUERY_STRING} _REQUEST(=|\[|\%[0-9A-Z]{0,2})
RewriteRule ^(.*)$ index.php [F,L]
This last bit of somewhat complex code helps to prevent database script injections. Every little thing we can do helps.
If any of these three code snippets mess up your site in any way, just simply go back to your .htaccess file and delete the code. Chances are that you put it in the wrong place, or that your theme or plugins don’t want to play along. That’s okay, but definitely give these snippets a try nonetheless!
If any of this is over your head, or if your site was already hacked, please feel free to get in touch with me here: https://theopguru.com/malware-cleanup/. I usually get sites cleaned up within 24 hours of being contacted, and you get some free tips, tricks, and consulting along the way.
Let the Comments Begin!
If you have any questions or comments, please do leave them below. I know that this is a hot topic, and people have tons of opinions on security. Please realize that this post does not mention everything, and does not claim to be the ultimate solution to WordPress security. It is simply a step in the right direction and will help greatly. With that in mind, comment away!











I am glad you guys fixed this and I hope I was helpful bringing it to your attention when it happen to me. I was so impressed how fast you guys were on top of this once it was confirmed.
It was fast because they found me… 🙂 (Did that horn just toot itself? Tsk, tsk…)
I went through Chris’s post and I got two questions
1) Does Host Gator have autobackup?
2) How do I delete a theme in WP? I can’t find the way to do that.
Francois,
To delete a theme you go to Appearance -> Themes and click on the image representing the theme you want to delete. A new window will pop up. In the bottom right corner you will see a link that says delete. If it is not there that means you are looking at the currently active theme.
Thank you Cindy!
Thanks for this, I was wondering the same thing.
As I said in the private Facebook group (but want to share here for everyone else):
1.) I would suggest submitting a support ticket with HostGator to see your options. You can definitely download a complete backup on-demand from your by going here: cPanel > Files > Backups > “Download or Generate a Full Website Backup”. That’s for certain.
2.) Cindy has already kindly answered the other question here. 🙂
I already performed a full backup. I know how to restore from the backup if there is a problem. (I did ask HG about that) I am within the .htaccess file as I type this reply.
My question meant exactly what it meant: Do I paste the 3 sets of code lines one after the other at the very top of the .htaccess file?
I think you’re in the wrong comment thread here. The answer is below: Yes, back to back should be fine, at the bottom or top. But make sure you are copying and pasting exactly what you see here. 🙂
Oh my! This is embarrassing! 🙁
Sorry about that…
No worries my friend. 🙂
Yes of course HostGator has auto backup BUT what if they only backup the version that’s hacked? What if you have too many inodes and they don’t do auto backups? CALL them, don’t ask us! I use HG and I NEVER ask others about HG. CALL, open a ticket, live chat. WHY do you pay money each month for a web host and not contact them?
Backups are a must, no matter what, hacked or not. If you’re hacked, you can’t just blindly restore a backup, that’s for sure. But without a backup, you have a serious problem if the hack destroyed your data. Point is, having a backup at least gives you options. You still need to be careful though, of course… Thanks for your input!
Chris,
I know this list isn’t supposed to cover all the things that can be done, but I was wondering what your thoughts on changing the login page addresses are? For example making it so you login somewhere other than /wp-admin or /wp-login. That is one of the big things I see people recommending and I was wondering if you see that as needed or not?
Great posts, I am off to change all of our passwords 🙂 Been meaning to for weeks…
That is useful, and definitely an added step you can take. I just didn’t want to make this post “The 25,342 Things You Can Do To…”, if you know what I mean. 😉
Here’s a plugin that does that though. Seems to have very good ratings and was recently updated (two very important things to look at whenever you select a plugin): https://wordpress.org/plugins/rename-wp-login/
Hope that helps!
About #12
Do i insert ALL the three sets of code lines one after the other, either at the very top or the very bottom of the .htaccess file?
Thank you!
Yes sir. That should be perfectly fine. Let me know the results here! (If your site doesn’t crash or go blank, everything should be fine. I’m here to help though!).
So far, seismic detectors are silent… 😀
Everything looks peachy-dandy.
Thanks a lot Chris!
Great news! Thanks for reporting back here. I thoroughly tested those code snippets on my own sites. I would never advise something that I haven’t used or tried myself. Sites, themes, plugins, etc., vary though, so it’s always best to try things out and then delete things if it causes problems.
Hey Chris great post! I know you didn’t want to make this article about “The 20,000,000″ things you can do to hack proof WordPress” but I always advise changing the security keys (salts) in the wp-config.php file as well.
Also, I can’t tell you how many times I see the “admin” username – right along with the easiest passwords ever like “test123” or even… “admin” haha.
If everyone reading this does everything that Chris says and nothing else your 99% ahead of everyone else who owns a WordPress site.
Great addition Kevin, thanks! Yeah, I could have literally mentioned everything about everything, but you have to stop at some point, right? 🙂
Anyone reading this, definitely consider changing your wp-config.php salts if you’re concerned or have issues, and definitely post-hack. You can read more about this issue here: http://digwp.com/2010/09/wordpress-security-keys/
Thank you very much for such useful info. It is good to know who to go to when a W Psite problem comes up.
You are very, very welcome Pamela. Glad you appreciated it. It means a lot. Spread the word, so hopefully we can get a handle on this mess that is going around! 🙂
Great Post. How would you rate protection services like Cloudflare?
Highly recommended. I use CloudFlare on all my sites. The free version is fine, unless you have an SSL (HTTPS) domain, then you need to pay. Thanks for asking!
Very good reading, thanks!
Just yesterday I had a talk with a friend, about deleting unused Themes and Plugins.
He said I saw ghosts in broad daylight.
Now I can show him that I’m not the only one. 🙂
To see if ghosts are real, try this test… Install the TwentyTwelve theme on one of your sites. Make sure it’s DEACTIVATED and not the active theme. Then browse here: http://YourSite.com/wp-content/themes/twentytwelve/style.css (replacing “YourSite” with your site address)… Hmmmm… what’s that? Wow, an inactive theme fully accessible?! Yep… #mindblown 🙂
Looks like you have to right-click on that link and copy it in order to see the full link. Full links don’t show here by default. Remember to replace the “YourSite” with yours. 🙂
Nice little trick, very useful to prove the point to my friend. Thanks!
You’re welcome!
Thank you. I have added the code to the .htaccess files of my blogs. I did learn the hard way how to protect my sites. I now use a firewall and other security plugins. Thank you for reminding me about deleting unused plugins and templates. 🙂 appreciate it.
You’re very welcome Connie! Yeah, believe it or not, but the number one reason for being hacked/infected is not updating (or leaving deactivated plugins and themes lying around), especially when security fixes are specifically released. For example, all you have to do is look at what happened a week or so ago with the MailPoet plugin — a major security issue was patched, and yet tons of users have still not updated! It just blows my mind. 🙂
what about backup plugins? Do they work? any suggestions?
…and thanks for the info Chris!
Oh, they definitely work, and are a must. That’s how I get things sent automatically to DropBox and Amazon s3 (well, I actually use InfiniteWP, but that’s another story for another day). If you want a free solution, I would recommend this: http://wordpress.org/plugins/updraftplus/
Thank you…
Thanks for the tips, I followed your instructions to reset my wordfence settings. I had already deleted the unused plugins now to delete the themes.
Awesome! And sorry for the late response here. 🙂
This was great blog. I am always concerned about security and there have been no easy answers, I just cant deal with code. Already broke my site once.
I tried Acunetix security and it changed some files from my website dashboard (that was nice).
Its just that it slows the site down so much.
Does wordfence slow the site down? Have you heard of any problems with it or its compatibility with plugins?
I really appreciated this energetic blog. SO now Chris, you are in my rolodex–yes rolodex!
Thanks for the positive feedback Mary!
WordFence may slow down your site while running a scan, but not other than that (and even that hasn’t been a problem for me). I run WordFence on 10 different sites on the same host, but my hosting account is really good though.
Thanks again for stopping by and for commenting! 🙂
I was using optimized press for my site and just switched to a wp theme. First I used tentyeleven and saw on mobile it was going to porn site so I switched to smartone. I was grateful for finding this blog. I have followed the steps and my site is still going to porn on mobile. Please help! Any suggestions?
Hello Jennifer!
Following this article is really only meant as prevention and general good website maintenence. For cleanup after-the-fact, there really is no better solution than to seek the help of a professional. If you would like me to take care of it for you in the next 24 – 48 hours, I would be happy to do so. Please find my services here: https://theopguru.com/malware-cleanup/
Thank you for the quick reply.
Thanks for this Matt.
1. What about Firewall settings in Wordfence?
2. Ive been trying to figure out this code in htaccess-
User-agent: *
Disallow: /wp-admin/ (Google Webmaster does not like it.)
Does it have a similar function as-
# protect wp-config.php file
order allow,deny
deny from all
?
3. Can codes like you posted here, be pasted in Mac text editor then pasted to htaccess to put the codes in the proper format? Or what is the proper way? I recently had an experience coping and pasting to htaccess and ended up with a white page that said: “You screwed up, that is why you no longer have access to your website.”
Hey there “Guest” 😉
A few thoughts:
1.) I didn’t really dig into those, but WordFence has a pretty extensive FAQ and guides on their website.
2.) Those are two different things. The “Disallow” one has to do with Google (and other search engines) indexing your site whereas the wp-config.php one has to do with your wp-config.php file on your server.
3.) Yeah, you have to know what you’re doing with .htaccess codes. I would copy paste from here, then into a plain text editor, save, and then copy/paste to your .htaccess file on your server from the plain text editor. Try at the top of your .htaccess file, but if that messes things up, put them at the bottom of your .htaccess file.
That’s about all I can help with here! 🙂
I apologize Chris. Thank you for the info! Thank you Matt, for the note!
No problem on the name mixup. I will comment on your other comment in a minute. 🙂
modafinil usa how to buy provigil order provigil provigil drug modafinil 200mg ca buy modafinil cheap modafinil us